Where Are the Attack Points in a Wifi Network
Understanding Rogue Access Points
One of the most common wireless security threats is the rogue access point—it is used in many attacks, both DoS and data theft. Many other rogue access points, however, are deployed by employees wanting unfettered wireless access—these access points are called soft access points. Other rogues are located in neighboring companies using your network for free access. Typically low-cost and consumer-grade, these access points often do not broadcast their presence over the wire and can only be detected over-the-air. Because they are typically installed in their default mode, authentication and encryption are not enabled, thereby creating a security hazard. Because wireless LAN signals can traverse building walls, an open access point connected to the corporate network the perfect target for war driving. Any client that connects to a rogue access point must be considered a rogue client because it is bypassing the authorized security procedures put in place by the IT department.
This topic includes the following:
What is a Rogue Access Point?
A rogue access point is a device not sanctioned by an administrator, but is operating on the network anyway. This could be an access point set up by either an employee or by an intruder. The access point could also belong to a nearby company.
These are some reasons to suspect that an access point is a rogue:
-
The SSID of the access point is neither your network SSID nor listed in the permitted SSID list. (See .) The access point may not be broadcasting an SSID at all. Check the SSID of an access point using any of these methods:
-
From the MSS CLI,
-
From Network Director, .
-
From MSS,
-
-
The access point is masquerading one of your SSIDs. Access points masquerading your SSID are rogue by default—you can, however, change that policy. See Understanding an SSID Masquerade.
-
The access point is an ad-hoc access point, formed directly between two client devices. See Understanding Ad-Hoc Networks.Ad-hoc access points are rogues by default—you can, however, change that policy—see Configuring Your Ad-Hoc AP Policy.
-
Network management features of the access point, such as SNMP, HTTP, and Telnet have been disabled.
-
The access point's MAC address does not appear in ARP tables.
-
The access point is operating as a bridge—see Understanding Wireless Bridging .
-
The access point is listed in the rogue list, where it has been added by an administrator.
How Are Rogue Access Points and Rogue Clients Identified By Controllers?
Wireless radios automatically scan the RF spectrum for other access points transmitting in the same spectrum. The RF scans discover third-party transmitters in addition to other Juniper radios. Controllers consider all non-Juniper transmitters to be suspects (potential rogues) by default. If the device is a Juniper device, but the MAC address is not in the appropriate database, a series of rules determine whether that device is a rogue. Once an access point is declared a rogue, it is reported by MSS:
-
From the MSS CLI,
-
From Network Director,
-
From MSS,
How are Rogue access points and Rogue Clients Classified as Rogue?
Controllers use a set of rules, illustrated in Figure 1, in order to classify unknown access points as either members, neighbors, suspects, or rogues.
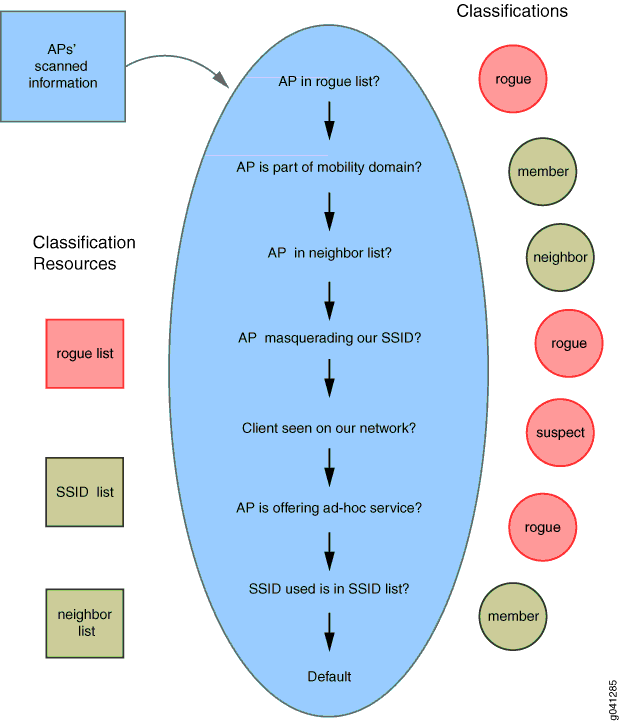
The definition of each classification-–member, neighbor, suspect, or rogue—is listed in Table 1.
Table 1: Classifications Define a Rogue
| RF Classification | Description |
|---|---|
| Member | Access point is in this mobility domain. Access point fingerprint (also referred to as signature) is used to securely identify member access points. |
| Neighbor | Trusted device (good neighbor) is listed in the permitted third-party SSID list. Usually, this access point is part of a neighboring wireless network or mobility domain. |
| Suspect | Not enough information to classify this access point as neighbor or rogue. You may decide to add it to the rogue list, SSID list or neighbor list. |
| Rogue | Rogue device (bad guy) on the air. For example, unauthorized access point on an enterprise network. |
You Can Change Some Rogue Classification Rules
Classification rules are either built-in or selected by you from a set of pre-defined rules. Built-in rules are constant and cannot be changed. User rules are the rules that let you configure certain classification behaviors.
Notice that the first classification rule eliminates access points in the rogue list and cannot be altered. Two configurable rules default to rogue classification and you can set a third to classify the default condition as rogue.
| User Rule | # | Rules for RF Classification | Classification |
|---|---|---|---|
| N | 1 | If access point in rogue list | rogue |
| N | 2 | If access point is part of mobility domain | member (never a rogue) |
| N | 3 | If access point in neighbor list | neighbor (never a rogue) |
| Y | 4 | If access point is Masquerading our SSID | rogue (default) |
| Y | 5 | Client or Client DST MAC seen in network | rogue (default) |
| Y | 6 | If access point is acting as an Ad-hoc device | skip-test (default) can be set to rogue |
| N | 7 | If SSID is in SSID list | neighbor (never a rogue) |
| Y | 8 | Default Classification | suspect (default) can be set to rogue |
What Harm Can a Rogue Access Point Do?
Rogue access points and their clients undermine the security of an enterprise network by potentially allowing unchallenged access to the network by any wireless user or client in the physical vicinity. Rogue access points can also interfere with the operation of your enterprise network. Rogue access points can do the following damage:
-
Allow a hacker to conduct a man-in-the-middle attack. The attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker.
-
Flood the network with useless data, creating a denial of service.
-
Send fake SSIDs advertising attractive features such as free Internet connectivity. Once a user connects, the fake SSID is added to the client's wireless configuration and the client begins to broadcast the fake SSID, thereby infecting other clients. .
-
Provide a conduit for the theft of company information..
What Can I do To Prevent Rogue Access Points?
There are a number of actions you can take that make it more difficult for a rogue to penetrate your network. See Table 2 for details.
Table 2: Preventing Rogue Access Points
| Do This: | Result of Action: |
|---|---|
| Establish strict rules and make sure they are well published. | Only authorized IT staff can connect networking equipment. All devices that connect to the network, including wireless access points, conform to company security policies. Note: Some colleges even expel students who are caught with rogue access points or ad-hoc networks. |
| Change the rogue classification rules. | By default, unknown devices are classified as suspects. When you change this default to rogue, the controller automatically classifies any third-party access point or client as a rogue, and you can optionally isolate the access point by dropping all packets to and from the device. |
| Eliminate benign access points from the rogue list so that real rogues stand out. | When you add safe networks' SSIDs and/or vendor names to the list of SSIDs allowed on the network, these access points cannot be classified as rogues. . |
| Add known intruders to the rogue list. | Third-party access points are isolated when they are added to the rogue list. All packets are dropped to and from access points. |
| Use strong security | The IEEE 802.11i security standard uses IEEE 802.1X for mutual authentication between the network and the client. This means that clients that try to access network resources must be authenticated by the network. In a similar vein, the client verifies the authenticity of the network infrastructure it is attaching to before beginning data transmission. With 802.1X, the credentials used for authentication, such as login passwords, are never transmitted without encryption over the wireless medium. In addition, 802.1X provides dynamic per-user, per-session encryption keys, removing the administrative burden and security issues associated with static encryption keys. Security is configured in WLAN profiles. |
| Use active access point scanning in addition to passive scanning. | Active scans send probes with a null SSID name to look for rogue access points and clients. Active scan is enabled by default on radio-profiles. We recommend that you do not change this setting. |
| Make sure the Juniper wireless signature is enabled and change it on a regular basis. | A wireless signature is a set of bits in a management frame sent by an access point as an identifier. If someone attempts to spoof management packets from a Juniper access point, Network Director can detect the spoof attempt. |
| Make sure logging is enabled and check log messages and traps for suspicious activity. | By default, a controller generates a log message when a rogue is detected or disappears. For details, see Collecting Logs for Troubleshooting. |
| Immediately investigate ad-hoc access points and either add security to them or eliminate them. | An ad hoc network is one that is formed directly between two client devices. Ad hoc networks pose a threat to the enterprise because the security checks imposed by the infrastructure are bypassed. One of the dangers is an employee who brings in a wireless-enabled laptop, plugs it into a wired port at work, and leaves the wireless interface enabled. In this scenario, a hacker in a neighboring area could connect directly to the client, creating a security threat. The hacker at this point could look for information on the employee's client device, and potentially gain access to the corporate network through the simultaneous wireless and wired interfaces. This situation may place the enterprise in violation of regulatory policies for its industry. The security hole provided by ad-hoc access points is not the ad-hoc network itself but the bridge it provides into other networks. |
| Immediately investigate wireless bridge frames and eliminate the source. | An attacker often sets up a laptop with two wireless adaptors—one card is used by the rogue access point and the other is used to forward requests through a wireless bridge to the legitimate access point. . |
| Use managed switches on your network and use their port-based security to allow only certain MAC addresses or disable unused ports. | An access point randomly plugged into ports on this switch will not work. |
| Consider using static IP addresses instead of having them assigned by a DHCP server. | When you use static IP addresses, an intruder who installs a rogue access point needs to manually assign an IP address to the access point before it can gain access to the network. |
| Enable automatic countermeasures to immediately react to rogues or suspect rogues. | Countermeasures can attack or isolate rogue and/or suspect transmitters using various methods of attack. |
How Do I Prevent a Benign Access Point From Being Classified as a Rogue?
access points belonging to your mobility domain are never classified as rogues.
Presence of third-party access points on a permitted SSID list or OUI list does not guarantee that the device will not be classified as a rogue for other reasons. The only sure way to be sure a non-mobility domain device is not classified as a rogue is to add the device or vendor to the neighbor list.
Neighbors are devices known to be part of a neighboring network and non-threatening. Vendors can also be added to the neighbor list, so that all of the devices from that vendor become neighbors.
Where Are the Attack Points in a Wifi Network
Source: https://www.juniper.net/documentation/en_US/junos-space-apps/network-director3.1/topics/concept/wireless-rogue-ap.html